Secure.Systems™, by SyncDog
The First:
Fully Integrated
End-to-End Mobile Security Solution

Tired of being chained to your desk?
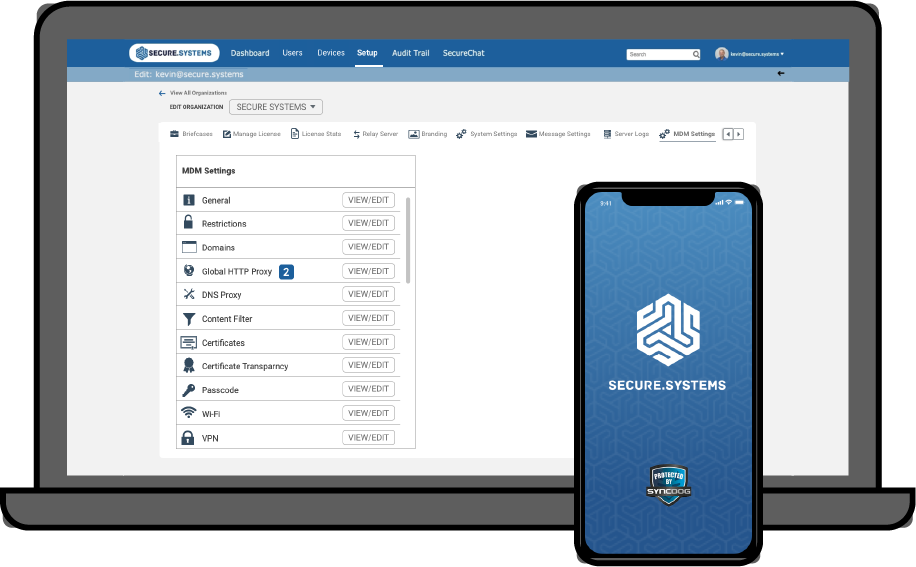
You need SyncDog’s Secure.Systems™. Secure.Systems™ is a mobile security solution built with the mobile worker in mind. Watch to learn how to turn your personal device into a mobile office.
SyncDog, when your old EMM solution just isn’t enough!
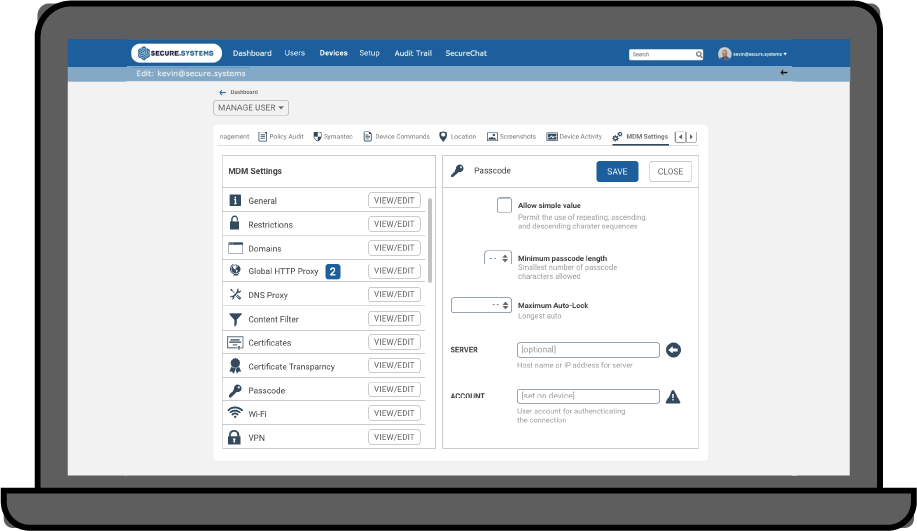
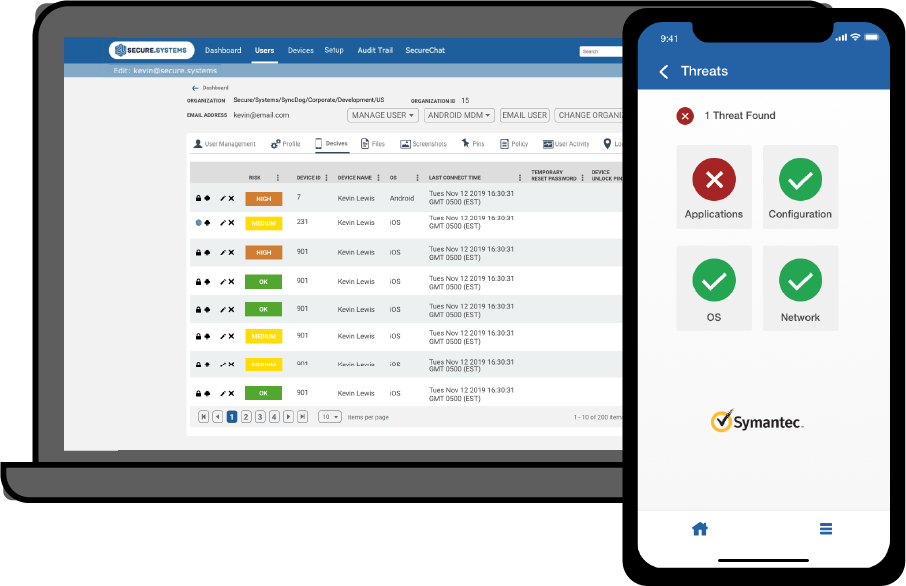
SyncDog provides one fully integrated modular solution that ensures…
Device Protection
Email & Data Encryption
Secure Support for BYOD
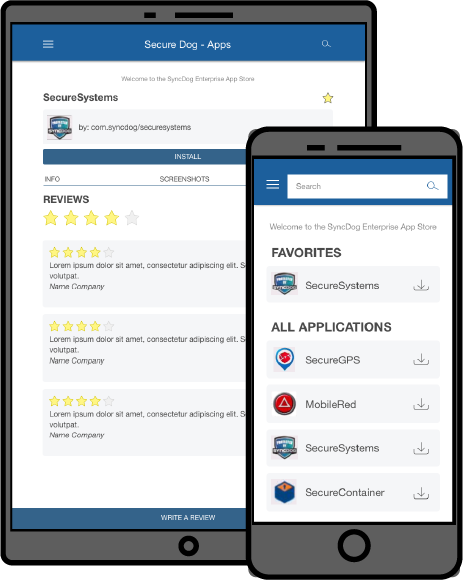
Native / Hybrid app store
Anti-Malware/Anti-Phishing
DLP / Dual Persona
IOS or Android
Role Based Functionality

Empower Your Mobile Workforce
A single instance of our Secure.Systems™ solution can be utilized across your mobile workforce as well as 3rd party contractors and consultants.
Secure Unmanaged
BYOD
The Secure.Systems™ Workspace provides a secure application platform for employees accessing enterprise mobile productivity apps on BYOD or CYOD (Choose Your Own Device) devices.
Increased Productivity & Security
Our solution finally removes the technological struggle of having to choose between increased security or increased productivity. SyncDog enables you to have both.
See How Secure.Systems™ Can Secure Your Mobile Workforce
News
Outdated Government And Commercial Security Policies Encourage Dangerous Workarounds
Mobile workforces requiring “anytime, anywhere” access are the established reality for many public- and private-sector organizations. And although comprehensive security policies go to great lengths to account for the devices and applications employees are using, gaps...
Developing an Effective Mobile Security Strategy
When developing policies for mobile devices, IT Leaders must be cognizant of security threats such as data leakage, spyware, and cryptojacking attacks. Enterprise Mobility Exchange spoke with Brian Egenrieder, CRO of SyncDog to explore this topic in more detail. Read...
What I Learned at Black Hat 2019 on Authentication, Workspace, and Security
Black Hat 2019 felt like a blur to me as I ran from meeting to session to meeting (while still finding time for the business hall). I sat down with over a half dozen vendors, some old and new to me, and attended several interesting sessions. While I continue to digest...
Blog
UAE Mobile Security Concerns in a Work from Home World
Only a select few companies, let alone countries, can say they were at the forefront of the work from anywhere movement prior to COVID-19. The United Arab Emirates (UAE) was not one of those select few. With an office-centric work culture, UAE companies typically...
SyncDog’s Mobile Endpoint Security Solution Earned Gold in the 17th Annual Cyber Security Global Excellence Awards
The past twelve months have been rife with corporate security compromises as enterprises realize how far they lag in their implementation of Zero Trust mobile security solutions for their remote workforces. Even as vaccines for COVID-19 rollout, many big name...
Switching to Signal: What You Need to Know About End-to-End Encryption
By: Jonas Gyllensvaan, CEO at SyncDog Whatsapp recently made headlines for a pop-up notification asking users to accept its new terms of use and privacy policy. While this sort of update isn’t out of the ordinary, it came as a surprise to most users that Whatsapp has...