SyncDog Whitepapers
SyncDog is the leading ISV for secure mobile workforce productivityMobile Security Solutions
Our whitepapers are written by industry practitioners with many years of experience and deep subject-matter expertise. Our whitepapers are free to download; we only ask that you provide a valid email address. To download a whitepaper, please provide your email address and then click the green button that appears below the email field to view the whitepaper PDF.
What happens to your information after you submit your email address?We store your name and email address to notify you of future software updates and blog postings. That’s it. We do not share data and as we are IT security practitioners, our data is secure. All communications emanating from SyncDog are CAN-SPAM compliant. Click here for the SyncDog Privacy Policy.
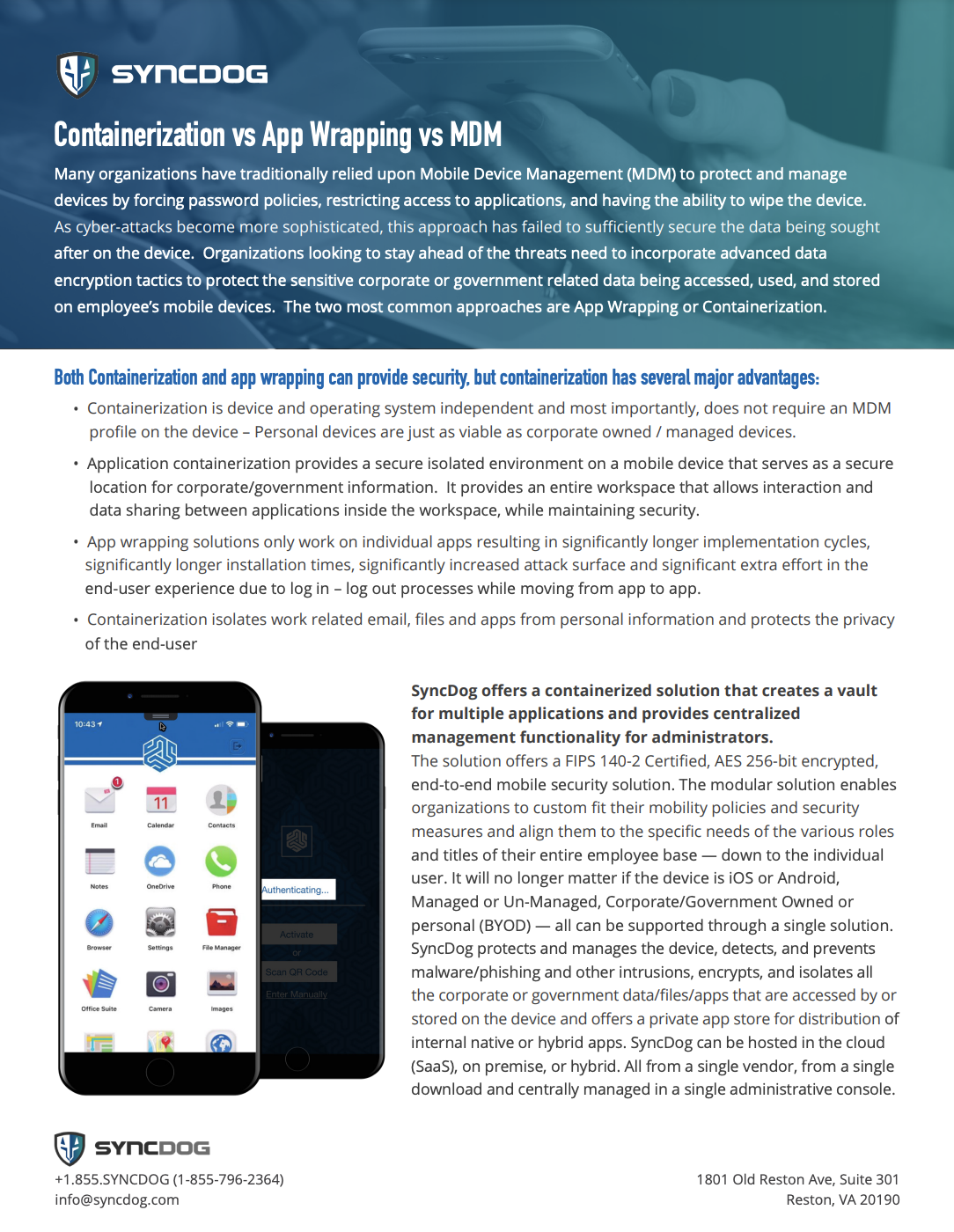
Containerization vs App Wrapping vs MDM
Many organizations have traditionally relied upon Mobile Device Management (MDM) to protect and manage devices by forcing password policies, restricting access to applications, and having the ability to wipe the device. As cyber-attacks become more sophisticated, this approach has failed to sufficiently secure the data being sought after on the device. Organizations looking to stay ahead of the threats need to incorporate advanced data encryption tactics to protect the sensitive corporate or government related data being accessed, used, and stored on employee’s mobile devices. The two most common approaches are App Wrapping or Containerization.
Download Whitepaper
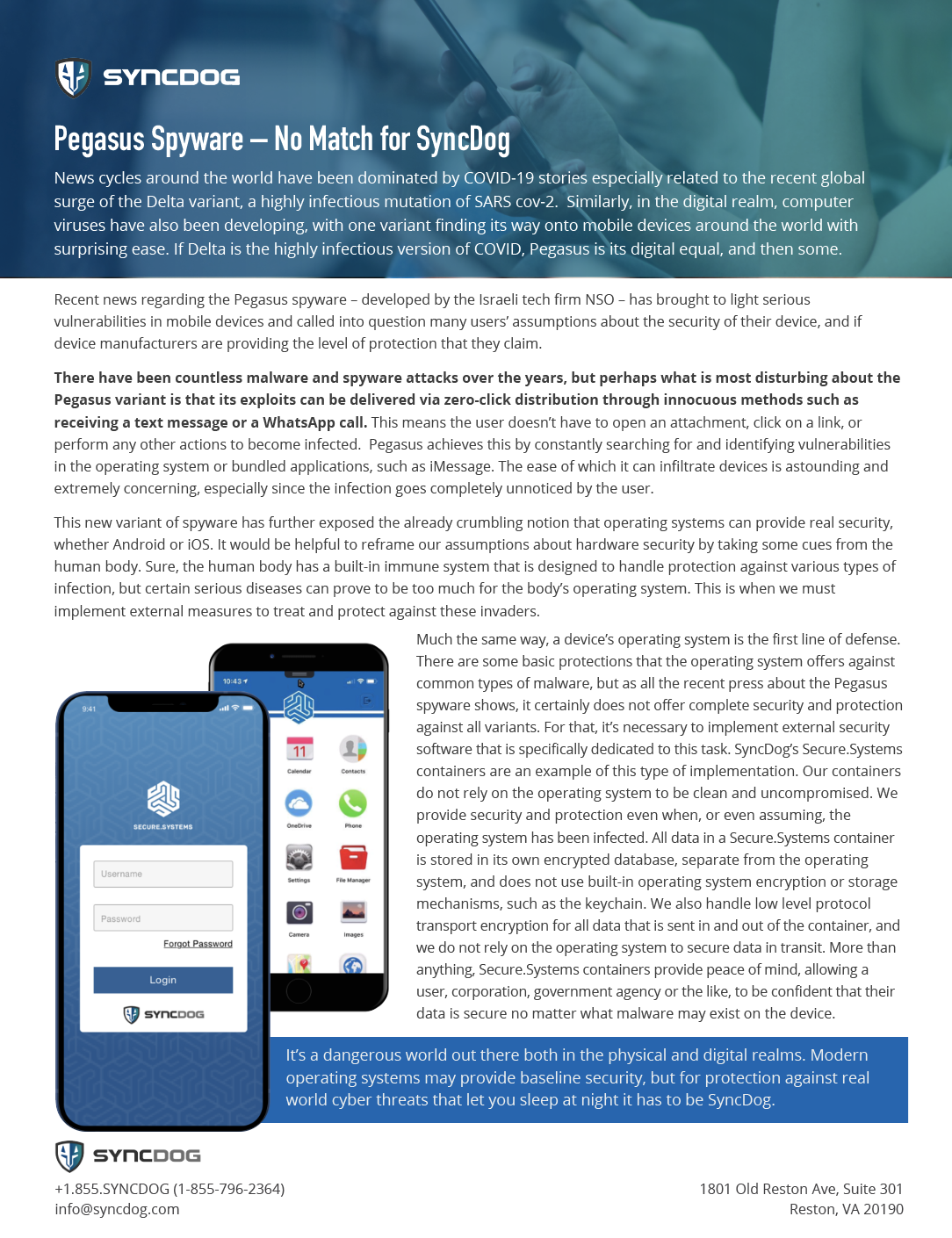
Pegasus Spyware – No Match for SyncDog
News cycles around the world have been dominated by COVID-19 stories especially related to the recent global surge of the Delta variant, a highly infectious mutation of SARS cov-2. Similarly, in the digital realm, computer viruses have also been developing, with one variant finding its way onto mobile devices around the world with surprising ease. If Delta is the highly infectious version of COVID, Pegasus is its digital equal, and then some.
Download Whitepaper

Cloud vs On-Premise vs Hybrid
There are some industry standards and government regulations that require corporations or government agencies to implement an on-premise solution. While other industries and government agencies have the flexibility to choose to host everything in a cloud environment. An on-premise implementation is one where the servers reside within an organization’s premises giving full visibility and control of the hardware, data and crypto keys to the data owners, where as a cloud implementation, a third-party hosts the hardware and often administers the set up and connectivity.
Download Whitepaper
Zero Trust – The Need for Zero Trust Is Driving Mobile Security Specialization
Enterprises have been trudging down the path toward a zero trust security model for a couple of years now, but the proliferation of mobile devices and remote work—and the risks associated with them—now has them sprinting toward the right solutions. The use of mobile devices is steadily growing, telework is increasingly common and mobile threats are becoming the biggest factor in the security landscape.
Download Whitepaper

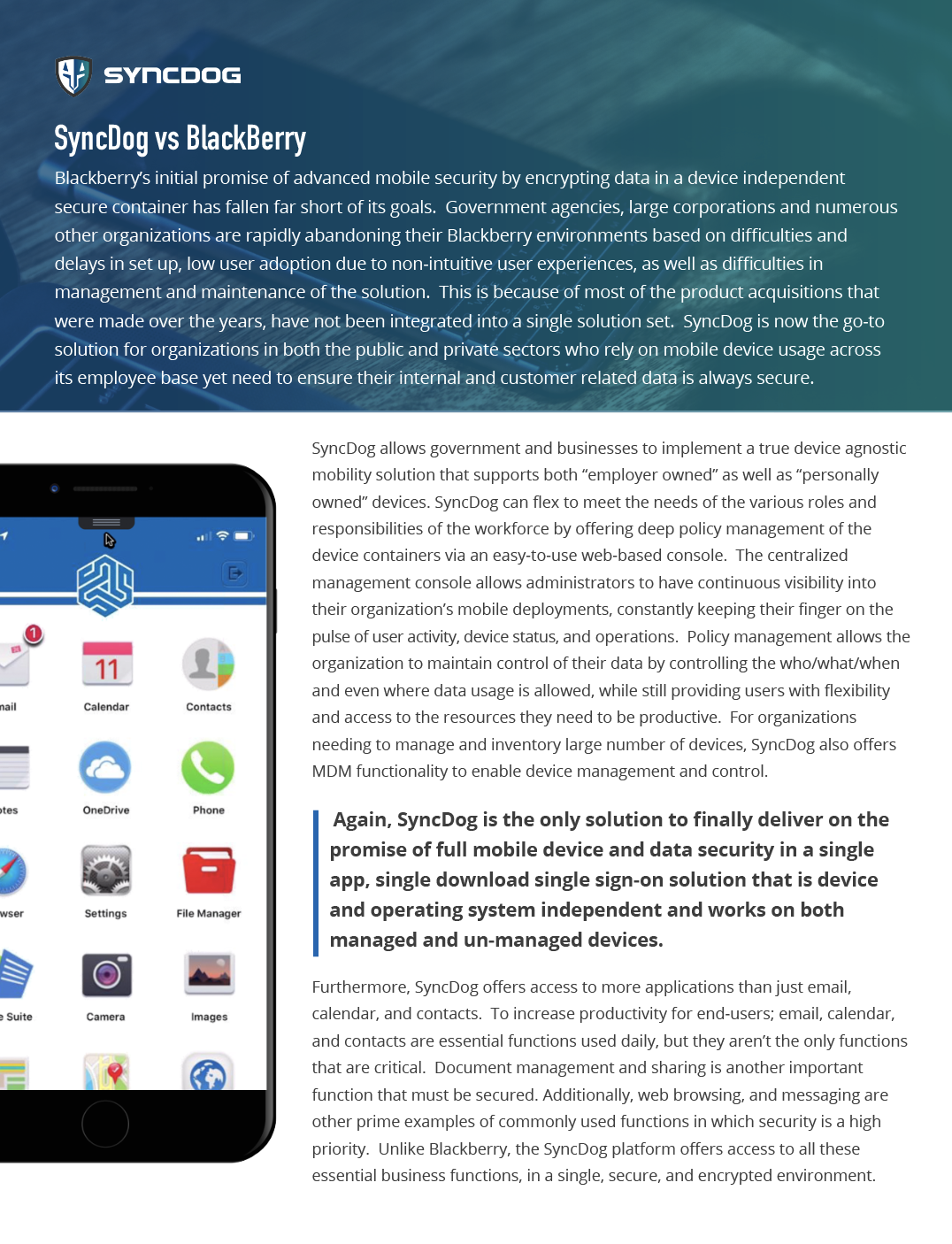
SyncDog vs BlackBerry
Blackberry’s initial promise of advanced mobile security by encrypting data in a device independent secure container has fallen far short of its goals. Government agencies, large corporations and numerous other organizations are rapidly abandoning their Blackberry environments based on difficulties and delays in set up, low user adoption due to non-intuitive user experiences, as well as difficulties in management and maintenance of the solution. This is because of most of the product acquisitions that were made over the years, have not been integrated into a single solution set. SyncDog is now the go-to solution for organizations in both the public and private sectors who rely on mobile device usage across its employee base yet need to ensure their internal and customer related data is always secure.
Download Whitepaper
For Mobile Security, Antivirus is a Band-aid, not a Solution
Today, mobile devices are nearly ubiquitous. According to the Pew Research Center, 95 percent of Americans own a cellular device of some kind and 77 percent of that share belongs to smartphone owners. Statista estimates that the number of mobile phone users will surpass the five billion mark in 2019. The vast majority of these mobile device users? Young people. The ones that make up the new workforce. It is of natural consequence that the popularity of Bring Your Own Device (BYOD) has increased exponentially in recent years. Enterprise organizations are coming to grips with millennial and Generation Z employees who won’t give up their devices or take a corporate-owned without a fight.
Learn about BYOD in this informative whitepaper titled “For Mobile Security, Antivirus is a Band-aid, not a Solution”
Download Whitepaper


BYOD Data Security Threat – Potentially Your Greatest Cyber Threat
Mobile devices are becoming ubiquitous in business, and for good reason. Systems demand mobility, and companies must move – often rapidly – while maintaining access to a wide variety of technologies. Lost BYOD smartphones from theft or staff negligence could be your biggest threat to data.
Learn about BYOD threat and how you can better secure your data in this informative whitepaper titled “BYOD Will be One of Your Biggest Threat Vectors in the Next 12 Months – Here are 5 Tips to Reduce BYOD Risk in Your Enterprise”
Download Whitepaper
GDPR will bring the Teeth that have been Missing in Data Security Auditing and Compliance.
Data security standards have been around for decades yet standards enforcement has been lacking. This paper explains why GDPR will change the playing field next year, what GDPR means for endpoint data management, and offer 5 tips to help maintain compliance. Are you/will you be prepared?
Learn more in this informative whitepaper titled “GDPR will bring the Teeth that have been Missing in Data Security Auditing and Compliance”
Download Whitepaper


6 Things That Will Accelerate Enterprise Mobility Security Adoption
IoT is here, fueling the fire for cyber risk via mobile sources. By 2020, there will be more than 1,000,000,000 M2M (yes, a billion plus!) connections, each device module capable of accessing your network by a malicious hacker. Are you/will you be prepared?
Learn more in this informative whitepaper titled “6 Things That Will Accelerate Enterprise Mobility Security Adoption.”
Download Whitepaper
SyncDog Correlation Whitepaper – Why mobile device event log correlation matters
A recent study by Gartner, Inc. projected that by the year 2018, 70 percent of mobile professionals will conduct their work on personal smart devices. The report cites three key operational challenges enterprises will have to deal with as more personal phones and tablets invade the workplace – governance and compliance, mobile device management, and security. Best-practice IT security dictates that you monitor event logs with a correlation engine to proactively manage cyber threats. Download this paper for more details on mobile device event log correlation.
Download Whitepaper

