Secure.Systems™, by SyncDog
The First:
Fully Integrated
End-to-End Mobile Security Solution

Tired of being chained to your desk?
You need SyncDog’s Secure.Systems™. Secure.Systems™ is a mobile security solution built with the mobile worker in mind. Watch to learn how to turn your personal device into a mobile office.
SyncDog, when your old EMM solution just isn’t enough!
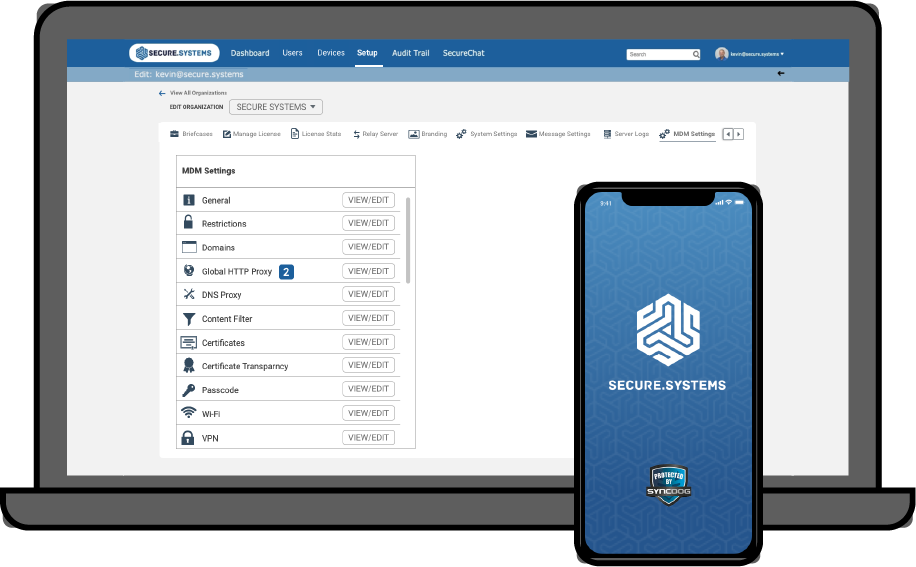
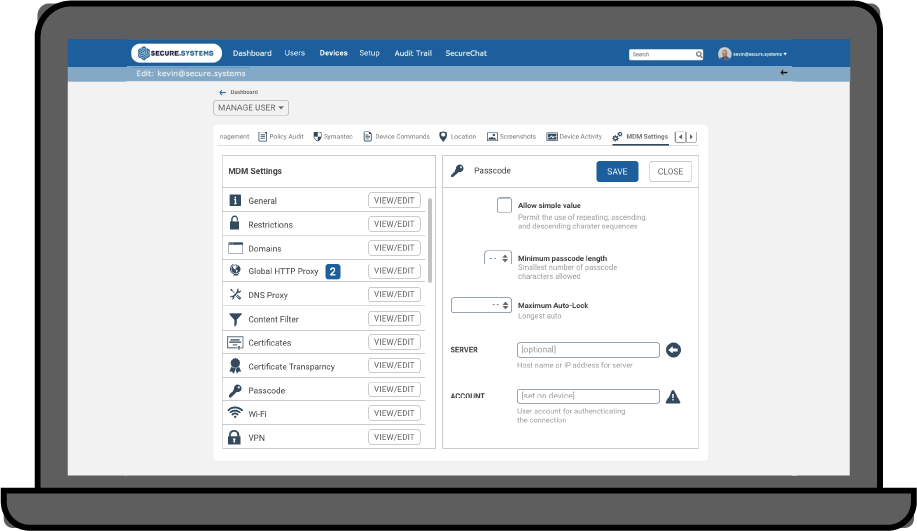
SyncDog provides one fully integrated modular solution that ensures…
Device Protection
Email & Data Encryption
Secure Support for BYOD
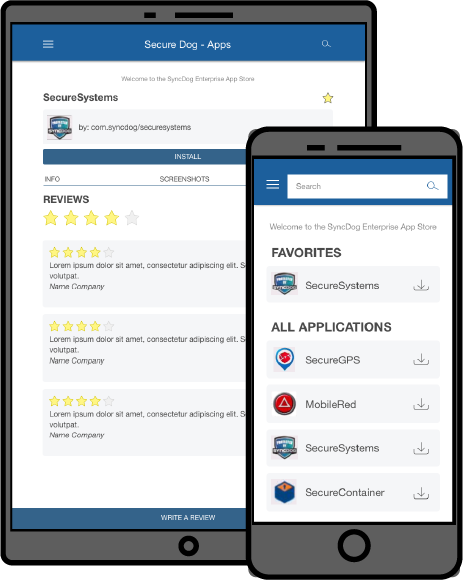
Native / Hybrid app store
Anti-Malware/Anti-Phishing
DLP / Dual Persona
IOS or Android
Role Based Functionality

Empower Your Mobile Workforce
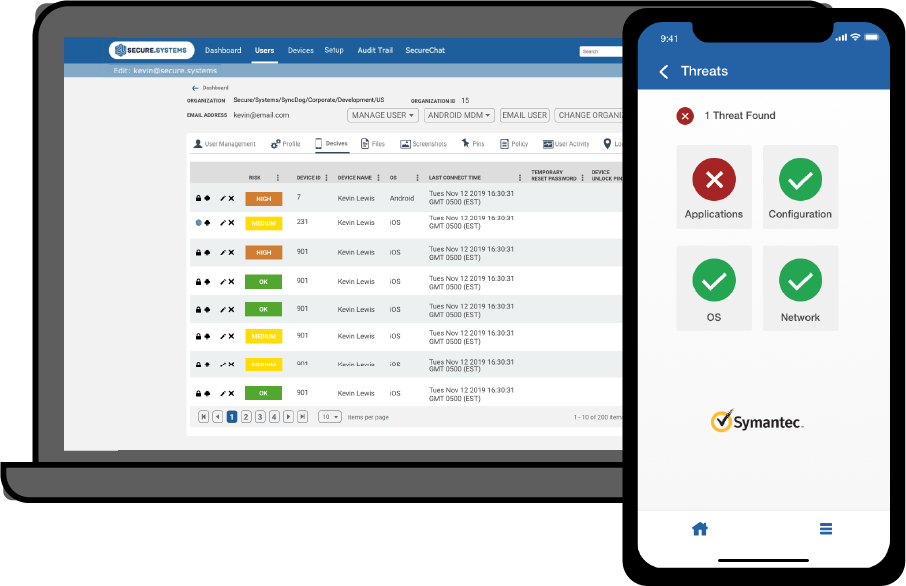
A single instance of our Secure.Systems™ solution can be utilized across your mobile workforce as well as 3rd party contractors and consultants.
Secure Unmanaged
BYOD
The Secure.Systems™ Workspace provides a secure application platform for employees accessing enterprise mobile productivity apps on BYOD or CYOD (Choose Your Own Device) devices.
Increased Productivity & Security
Our solution finally removes the technological struggle of having to choose between increased security or increased productivity. SyncDog enables you to have both.
See How Secure.Systems™ Can Secure Your Mobile Workforce
News
SyncDog Inc. Enables Mobile Workforce Productivity Through Data Loss Prevention Application
RESTON, Va.--(BUSINESS WIRE)--SyncDog Inc., the leading Independent Software Vendor (ISV) for next generation mobile security and data loss prevention, provides the mobile workforce with an integrated, brand agnostic platform that supports and expands productivity so...
SyncDog, Inc. Announces How to Improve Your EMM, with Live Demos at Upcoming HIMSS 2019 Conference
SyncDog announces its latest version 4.1, featured on the new iPhone XR, with live demonstrations at HIMSS Orlando, February 11-15. Reston, VA, January 25, 2019- Your EMM isn't enough! Let SyncDog show you how to make BYOD a success again without the overreaching...
The CyberWire Daily Podcast
In today’s podcast we hear how Fancy Bears and free-range catphish have been disporting themselves in the Czech Republic. China reported to have used watering hole attacks to gain entry into Australian institutions. Quora suffers a data breach. Marriott’s breach...
Blog
6 Security Considerations for Remote Work Amidst the COVID-19 Outbreak
By: Brian Egenrieder, CRO, SyncDog COVID-19 is top of mind for everyone around the world, from both a personal and professional perspective. People are canceling travel plans, avoiding public spaces and requesting to work from home. As the outbreak spreads, businesses...
RSA 2020 Recap: 3 Key Themes
By: Jonas Gyllensvaan, Founder and CEO, SyncDog RSA Conference is known for the breadth and depth of cybersecurity expertise it draws to San Francisco each year. From the double Expo floor to speakers and sessions, the four-day-long conference is a whirlwind. While...
How to Manage the Data Security of Third-Party Contractors
By: Brian Egenrieder, CRO, SyncDog Stuff happens. When you run into a situation that requires bringing more hands on deck, quickly, one of the last things you want to worry about is managing data security with a third-party contractor. Collaboration and Concerns The...