Secure.Systems™, by SyncDog
The First:
Fully Integrated
End-to-End Mobile Security Solution

Tired of being chained to your desk?
You need SyncDog’s Secure.Systems™. Secure.Systems™ is a mobile security solution built with the mobile worker in mind. Watch to learn how to turn your personal device into a mobile office.
SyncDog, when your old EMM solution just isn’t enough!
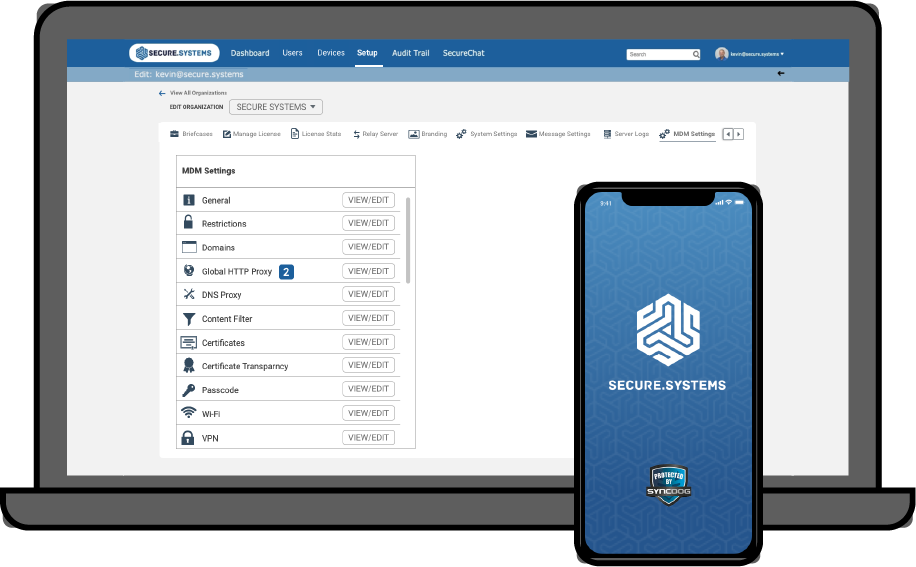
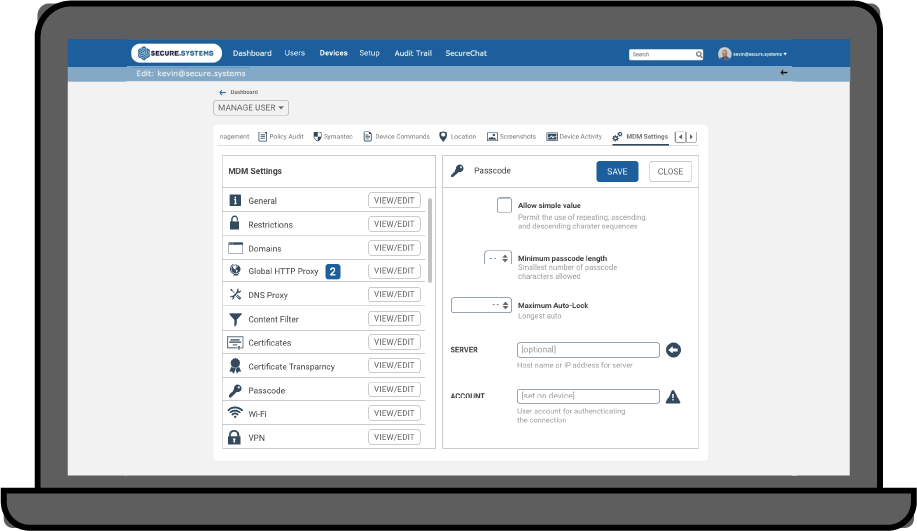
SyncDog provides one fully integrated modular solution that ensures…
Device Protection
Email & Data Encryption
Secure Support for BYOD
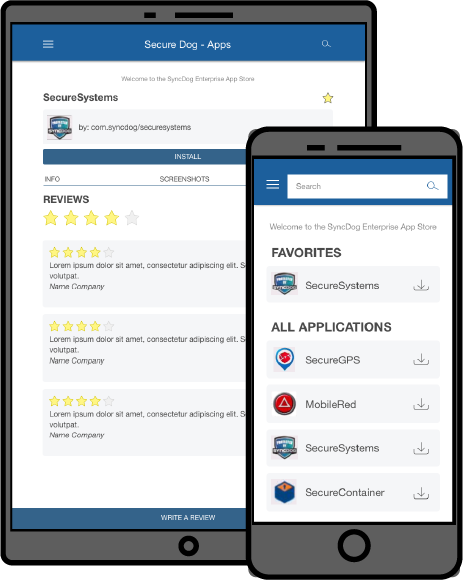
Native / Hybrid app store
Anti-Malware/Anti-Phishing
DLP / Dual Persona
IOS or Android
Role Based Functionality

Empower Your Mobile Workforce
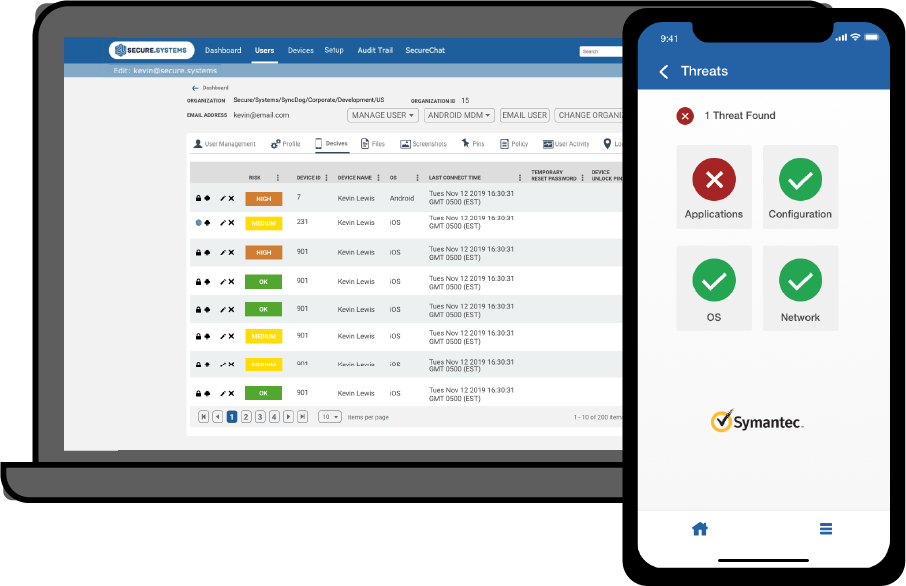
A single instance of our Secure.Systems™ solution can be utilized across your mobile workforce as well as 3rd party contractors and consultants.
Secure Unmanaged
BYOD
The Secure.Systems™ Workspace provides a secure application platform for employees accessing enterprise mobile productivity apps on BYOD or CYOD (Choose Your Own Device) devices.
Increased Productivity & Security
Our solution finally removes the technological struggle of having to choose between increased security or increased productivity. SyncDog enables you to have both.
See How Secure.Systems™ Can Secure Your Mobile Workforce
News
Mobile Security Policy Update
Mobile security in the enterprise, though not a new issue, is an increasingly serious subject today as mobile threats become better understood. Offering perspective, Pradeo just released a Mobile Security Threat Report that contained some eye-opening findings. Their...
Is Using Public WiFi Still a Bad Idea?
Security experts have long advised people to avoid using public WiFi networks because of the risk of being hacked. Despite those warnings, free WiFi is becoming more widespread and popular, with consumers browsing the web courtesy of local governments, cable...
Adhering to the mobility requirements of NIST 800-171 does not have to keep you awake at night
The majority of companies in the United States and Europe are required to comply with at least one IT security regulation – often times more. This forces companies to exert strong control over how data is transferred, accessed and maintained throughout its lifecycle....
Blog
A Look at 2020’s Mobile Security Threats Thus Far
By: Brian Egenrieder, CRO, SyncDog Each year mobile security threats get more complex. At the beginning of 2020 we detailed seven mobile security threats to be aware of -- social engineering, public wi-fi networks, OS vulnerabilities, apps, human error, SMS and voice,...
Stop Fighting the Battle to Ban Apps — Do THIS Instead
By: Brian Egenrieder, CRO, SyncDog We live in a tech-centric world. On average, U.S. households contain 10 internet connected devices. When it comes to using some of those devices for work-related activities, employers start to sweat. The constant concern centers upon...
Working from Home Securely: Employee and Leadership Perspectives
By: Brian Egenrieder, CRO, SyncDog Over the last decade, the concept of working away from the traditional office environment has become more common. In 2016, approximately 43% of employees worked remotely on occasion. The onset of COVID-19 has drastically changed...